Alongside the finance and insurance industries, the pharmaceutical industry is one of the financially strong sectors of the economy. Considering the large sums of money invested in researching new medicines, it is all the more important to protect all data from unauthorised third parties. Both technical and organisational measures must be implemented. Technical measures include securing networks with a suitable IT infrastructure or firewalls. Organisational measures include documentation and training for employees.
The 2021 State of Pharmaceuticals and Cybersecurity Report1 by Fortinet finds that an industry is rapidly losing the race to secure and protect intellectual property, business continuity and mission-critical data. 98% of pharmaceutical companies surveyed have experienced at least one breach. And about half of the companies surveyed experienced between three and five attacks in the last year (2020).
Cyber security in the GMP environment as a special challenge.
The particularly strongly regulated GMP environment does not exactly make it easier for cyber security. For example, no undocumented changes may be made to systems. And the installation of updates must also be based on a concept that is usually based on documents such as risk analyses, equipment and software lists. All efforts then result in (at least) one work instruction that describes in clearly defined scenarios how and when which updates may be applied to which systems. In addition, regular reviews of documentation and audit trails are carried out.
The attackers' methods evolve accordingly, incorporating current protection mechanisms. For this reason, cyber security in the company requires a system that also evolves and is subject to a life cycle process. Cyber security should therefore by no means be understood by companies and employees as an additional requirement. Rather, it must be part of the daily routine of a regulated IT. This also includes the sensitisation of all employees to the topic.
An Information Security Management System (ISMS) is therefore essential.
Protecting data is one side of the coin, the other is ensuring the confidentiality, availability and integrity of the data. The necessary rules, tools and processes are defined in the information security management system.
The implementation of security standards and the associated compliance with governance in the company, as well as the minimisation of risks through the use of process-oriented methods, is only successful if the following components are incorporated into the ISMS:
- Technical measures
- Organisational measures
- Cyber security concept
- Life cycle process
The life-cycle process (continuous improvement process) is an integral part of the information security management system. Security is made up of a mix of technology, measures, personnel and processes. But training and awareness-raising for the topics of cyber security and information security also play an important role in the context of a holistic process.
This means that you should audit and check yourself regularly.
An attack can pursue different goals.
An attack can have different targets and thus different effects. Furthermore, an attack can pursue several targets in parallel:
Target | Impact |
|---|---|
Delete data |
|
Manipulate data |
|
Spying on data |
|
Scattering of
Misinformation |
|
Tab. 1: Attack targets and effects.
The deletion of data.
The deletion of data is critical in the GMP environment. Years of investment in studies and complete documentation form the backbone of a product's approval. If attackers delete the data and the process has to be started all over again, a company can quickly reach its financial limits. If products are already on the market, but the quality of the manufacturing process cannot be traced, this can lead to expensive product recalls. The violation of regulatory requirements automatically leads to non-compliance, which can quickly result in warning letters from the FDA and a serious loss of reputation.
The manipulation of data.
The potential danger of data manipulation is even higher than data deletion. Deletion of data is generally noticed more quickly than manipulation. Deleted data does not mean that the quality of the product is subsequently poor. However, the manipulation of data can have a very strong impact on the product quality. This can go so far as to endanger the safety of patients.
Spying on data and spreading false information.
Spying on data and spreading false information is more likely to cause economic damage to the company and damage its reputation. Here, too, the severity of the attack in combination with the media interest and the level of awareness of the company can lead to insolvency.
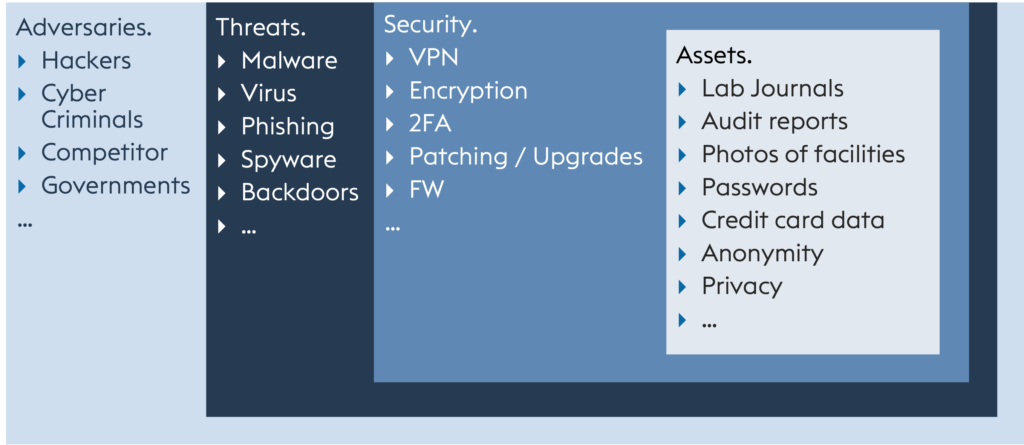
Assets.
The asset group defines which data is to be protected. This can be documents, reports, photos, but also password information or credit card data.
When choosing assets, the following questions are helpful:
- What data is most confidential for you? Not all data is equally confidential. Work with confidentiality levels. Depending on the level, the protection effort is defined.
- What data must not be lost under any circumstances?
Create categories and evaluate them. Data that must not be lost may be found in business/management, in the laboratory, in the research area or even in production.
- What would cause the most damage?
Define damage scenarios and subdivide e.g. by probability of occurrence, probability of detection, impact on different areas and criticality. Pay attention to a data-related assessment. The greatest damage occurs when what happens to what data?
- What could have a strong negative impact on the company's reputation?
Determine which scenarios can negatively affect the company's reputation. Classify the scenarios. Not every scenario affects the reputation to the same extent.
Anonymity / Privacy.
Privacy and anonymity also play an important role in the choice of assets.
Anonymity = moving around the network undetected
Privacy = secret data (Top Secret, Confidential)
Anonymity means that every user action is separated from the identity. Although it is possible to see which action has been carried out (e.g. an entry in a public forum), it is not possible to assign the user to a specific person.2 possible.
Privacy refers to data and its protection. Secrets should be kept. For example, it makes sense to make important business data accessible only to a certain group of people. Sending encrypted data is also part of privacy. If you load encrypted data into the cloud, the company is not anonymous as a customer, but the data is protected by the encryption and only those who have the key can decrypt the data.
In summary, assets are the data we have to take care of. They form our assets. The questions listed above, as well as the weighting of the areas of anonymity and privacy, can help in the creation of assets.

Security.
Different security procedures are used to protect the assets. For example, a VPN (Virtual Private Network) can secure the connection between sender and receiver. 2-factor authentication is also part of the security procedures, as is a firewall or the patching of computer systems (hardware and software).

Security is the degree to which our assets are resistant to threats. We select security controls based largely on the threat scenarios triggered by attackers.
Threats.
The threats represent the actual attack scenario. Besides attacks by means of viruses, Trojans, etc., phishing is also one of the threats. These threats are controlled/triggered by the attackers.

Exploits and Weakness.
The various threats are collectively referred to as an exploit. An exploit will attempt to exploit known vulnerabilities and thus gain access to systems. The vulnerabilities form the boundary between threats and security.
As soon as the exploit wants to penetrate the security zone, the security measures must take effect. To do this, the security system must first recognise that an attack is taking place. There is no such thing as 100% protection. A residual risk always remains. If the exploit has successfully penetrated the security zone, it will try to break through the next line of defence. Once the boundary between security and assets has been breached, the assets are accessed.
Vulnerability.
With vulnerability, we talk about the reasons why an attack could be successful in the first place. Depending on what data needs to be protected and to what extent, the appropriate security procedure must be established. Not all security procedures are suitable for all scenarios.
For example, a computer is infected with a spy tool because no security updates were previously installed. A VPN connection between the computer and the update server would not have prevented the attack here.
The vulnerability for the infestation is thus the omitted update.
Adversaries (opponents/attackers).
Once you have determined the assets and defined the security measures, you may want to explicitly protect yourself from certain threats. For this purpose, a threat landscape is created and the adversaries are included.
This way you can show in detail that you want to protect yourself from hackers, for example. Hackers often use backdoors such as security holes in applications. Security patches and updates provide a remedy. This would enable you to protect sensitive audit reports, among other things.
The attack vector.
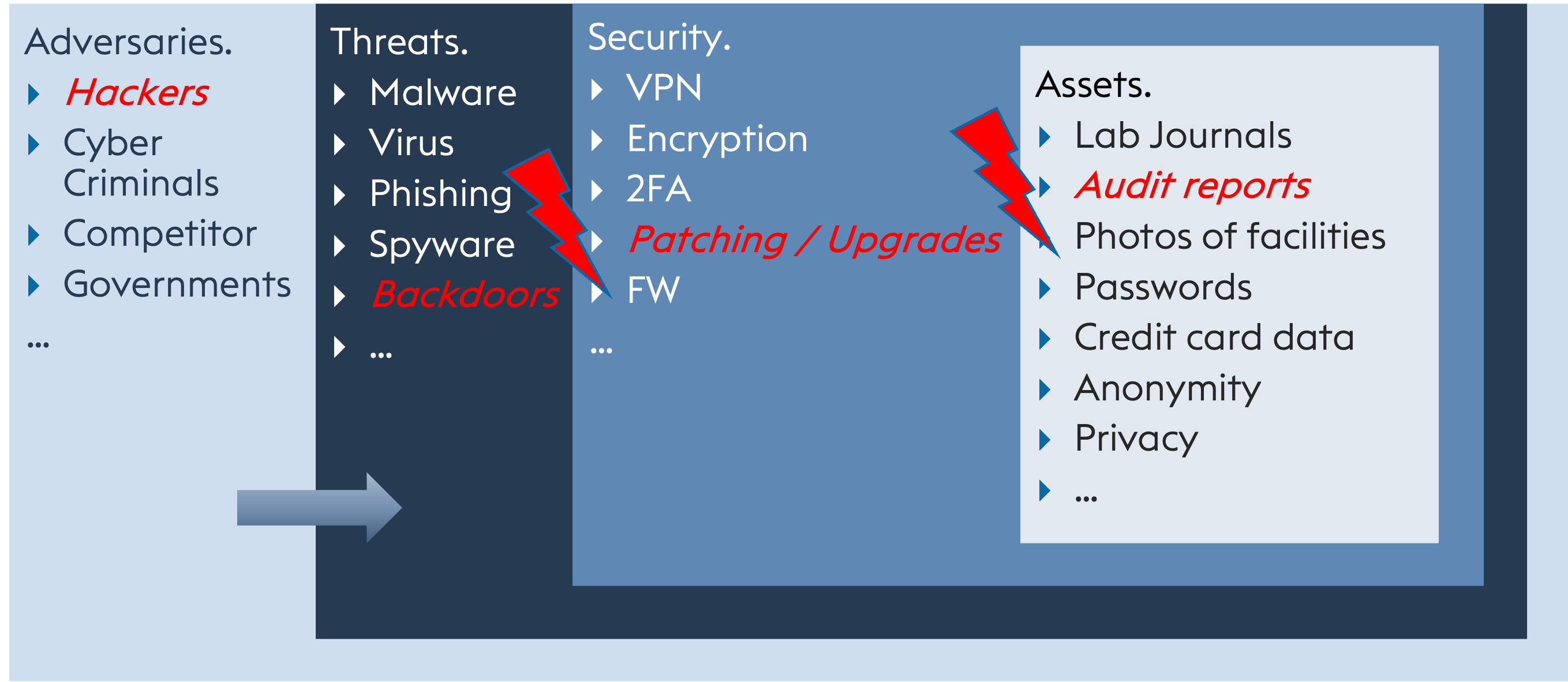
However, attack vectors can also be used in a completely different way:
A company notebook with highly sensitive data is stolen. A VPN connection is completely useless in such a case. The perpetrator theoretically has an infinite amount of time to access the data, since he is in possession of the notebook. Only a very strong and secure encryption of the entire notebook hard drive can help here.
The question when planning the security concept is:
How high is the impact if the encryption is cracked?
All devices with corresponding security measures must be checked regularly. Due to the constantly changing threat situations, measures taken are sometimes no longer sufficient after just a few weeks.
The added value.
The ISMS ensures that data can not only be used but also monetised within a legally defined framework. In the pharmaceutical industry, cautious trends are emerging to strengthen sales with data.
Every company that stores or uses customer data must be able to show the customer which data is used for which purpose. Especially with regard to data-based business models, it is to be expected that a functioning ISMS will become mandatory.
Other advantages of the ISMS are:
- Controllability of the safety aspects through process-controlled procedures
- Compliance with safety standards
- Fulfilment of corporate guidelines with regard to compliance/governance
Abbreviations.
2FA
FDA
FW
GMP
ISMS
IP
IT
VPN
2-factor authentication
Food and Drug Administration
Firewall
Good Manufacturing Practice
Information Security Management System
Internet Protocol
Information technology
Virtual Private Network
Notes and literature.
- https://www.fortinet.com/content/dam/fortinet/assets/analyst-reports/report-state-of-pharmaceuticals-and-cybersecurity.pdf
- In computer networks (company network, Internet), the IP address and other measures make it possible to identify a user (or at least the workstation).
